How to set up an AWS IAM user to use with Sovy - Guide
Table of contents
- Introduction
- Creating AWS IAM user
- Setting user details
- Attaching correct permissions policy
- Generating credentials
- Summary
Introduction
To integrate your Amazon SES account with the SES email templates manager Sovy, you'll need to set up an AWS IAM user with specific permissions. This guide provides a step-by-step explanation of creating and configuring an AWS IAM user and generating the necessary credentials (AWS Access Key ID and AWS Secret Access Key) for Sovy.
Creating AWS IAM user
First, you need to create an IAM user for Sovy - so it will have access to manage your templates, identities, and other SES settings. Enter "IAM" into the searcher at the top of the AWS console and click the IAM service. It will take you to the IAM dashboard.
In the left-side navigation bar, you will find a link Users - click it! Now, you may already have a few users on the list but it is a good practice to have a separate user for each external service that needs access to your AWS, so we will create a new one.
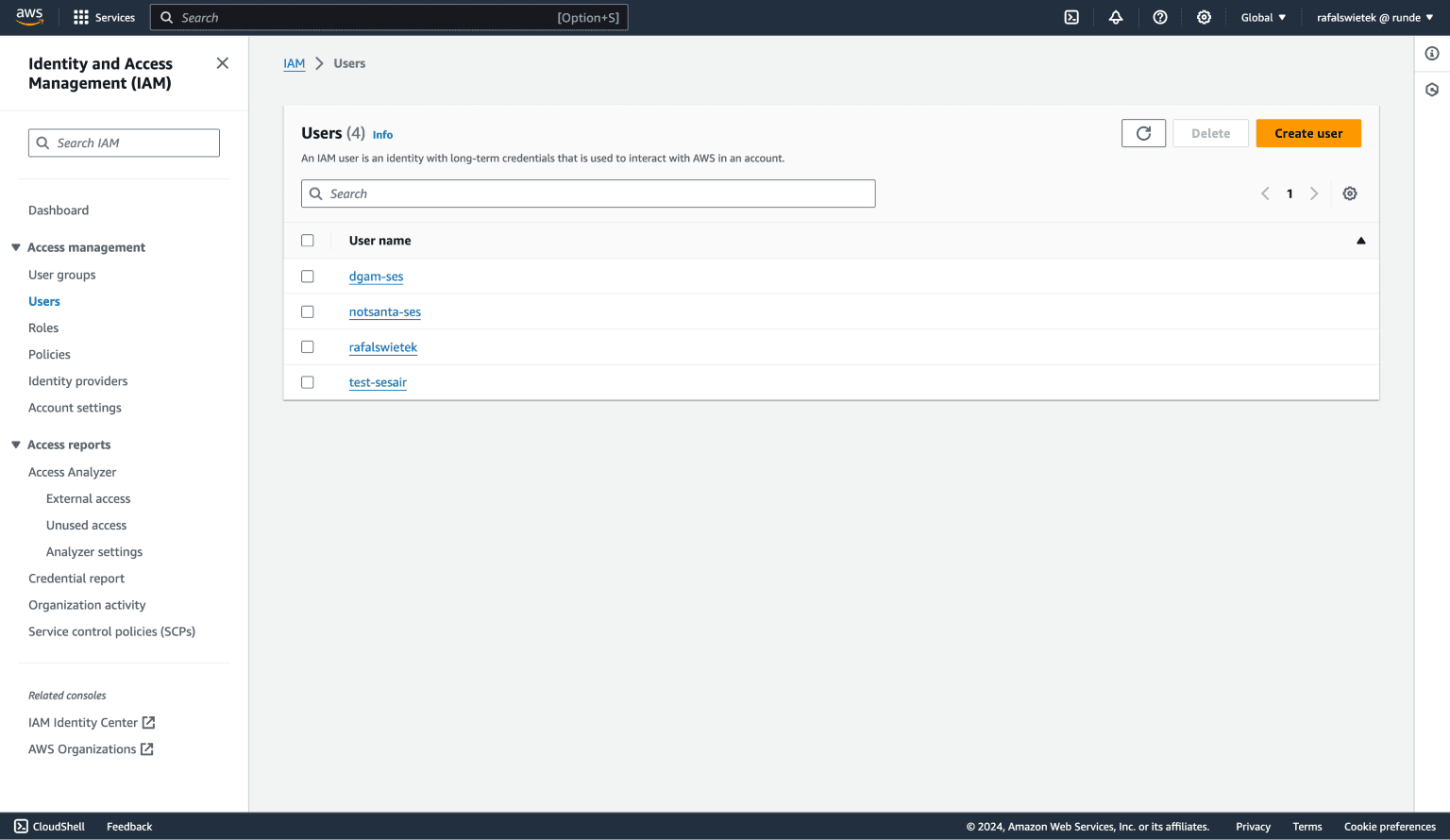
There is an orange button Create user above the table. Let's click it.
The full process of creating an IAM User is divided into 5 parts - each one of them is super short and easy to complete.
Setting user details
On the first screen, we just need to enter the user's name.
The available option - Provide user access to the AWS Management Console - is for users that will need access to the AWS console (the same console you're in right now). Sovy only needs programmatic access so we should leave this option unchecked.
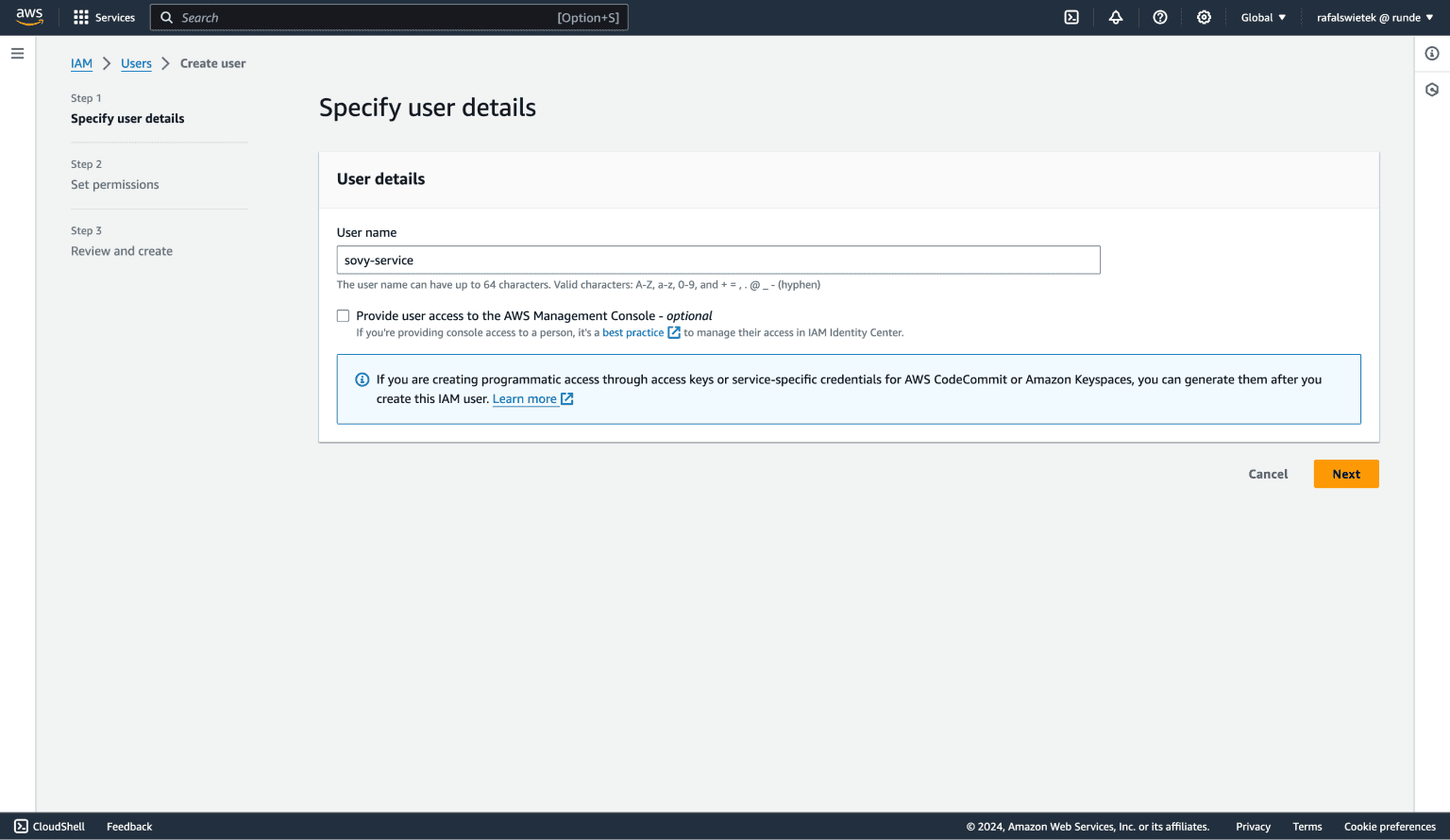
After we're done here click the orange button saying Next.
Attaching correct permissions policy
The next step allows us to set permissions for our user, which in our case is the template manager. It requires partial access to AWS SES service to fully manage your templates, and display important information about your account, some statistics, etc.
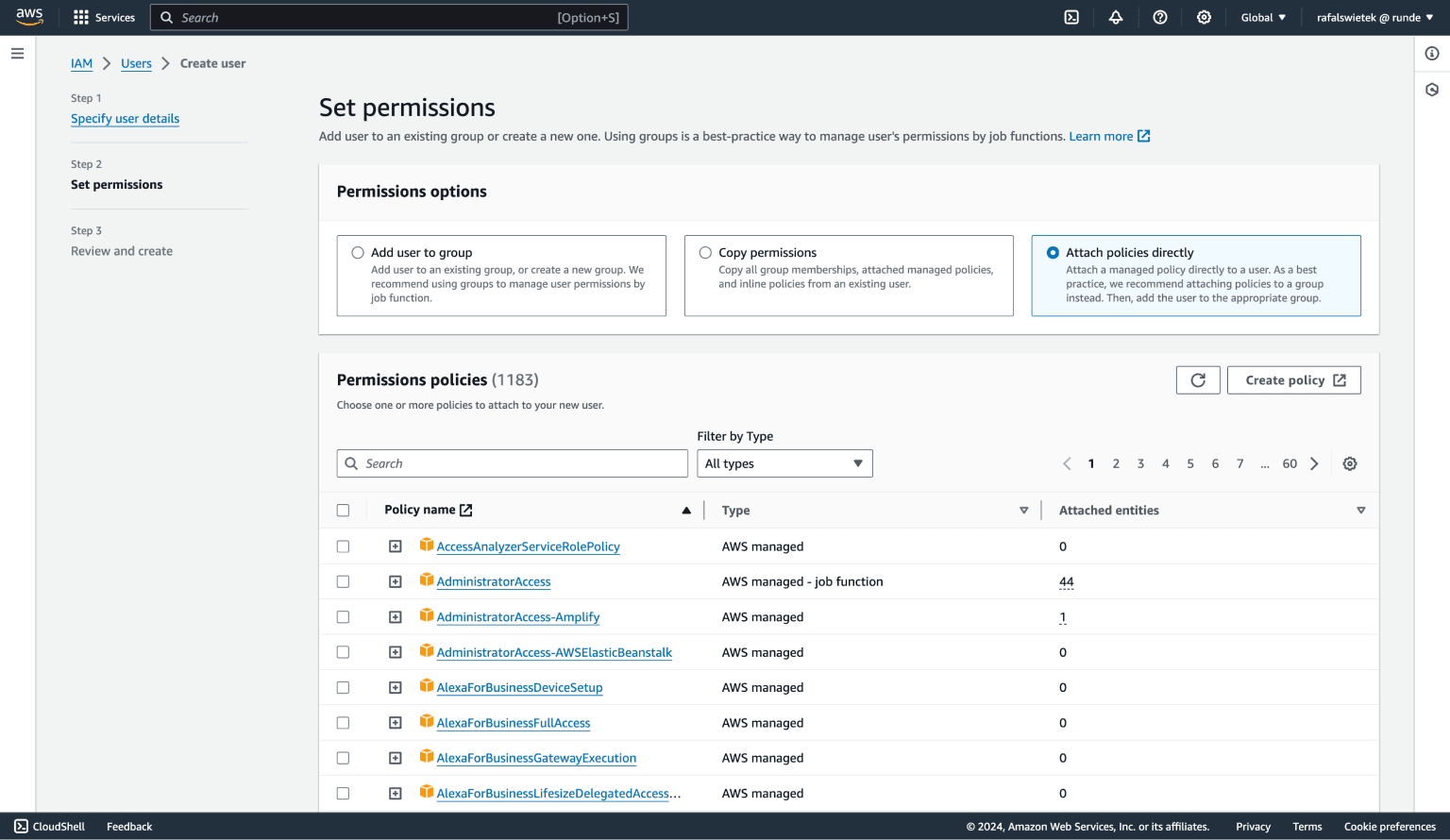
Start by clicking the Attach policies directly button. Then, click the Create policy button above the policies table. It will open a new browser tab with a policy editor.
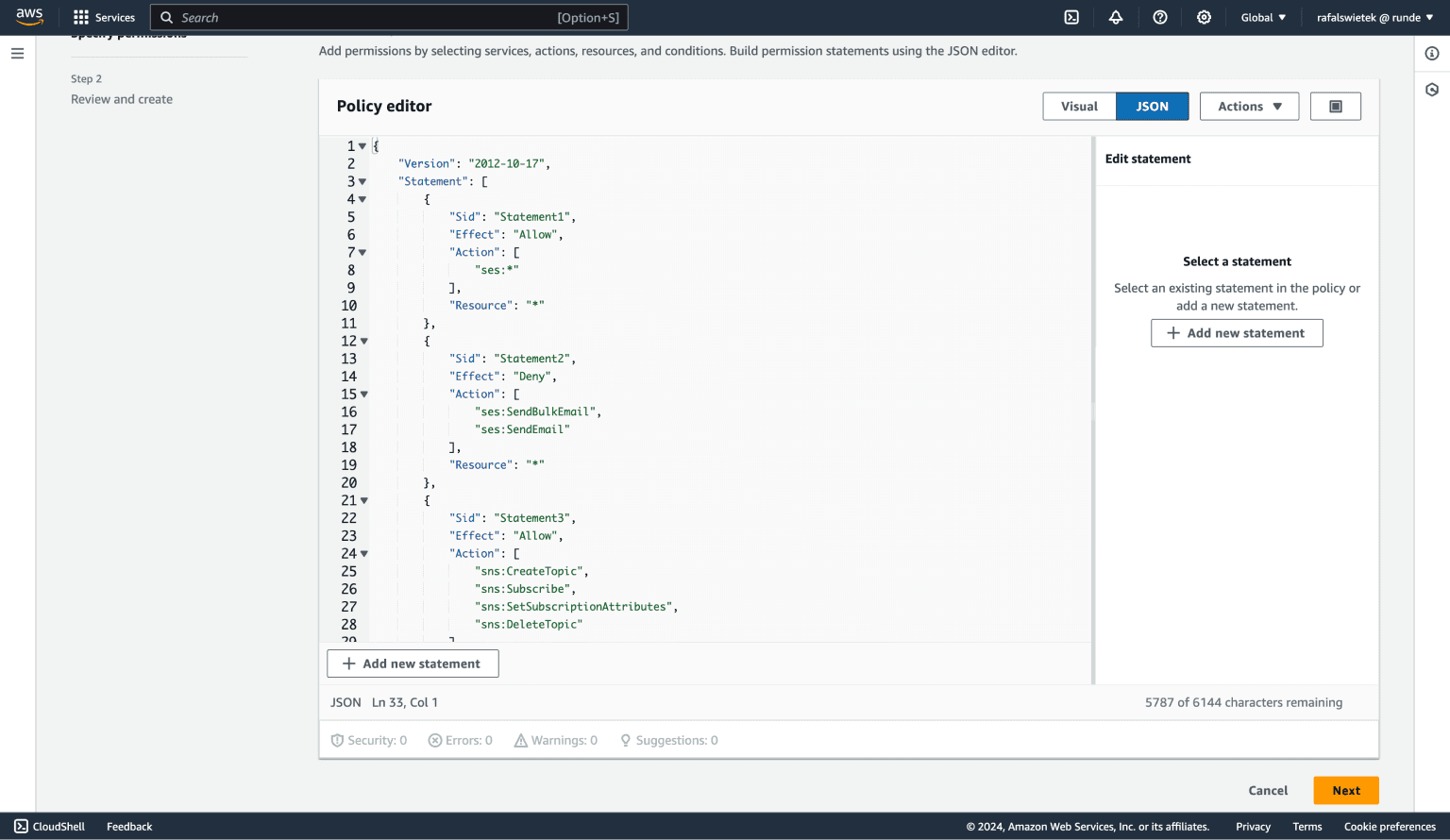
First, set a name for your new policy, e.g. AmazonSESTemplatesManagerAccess. Next, in the policy editor, select the JSON mode instead of Visual and enter a permissions policy in the big text area.
This is a permissions policy that we recommend to use with Sovy:
Click the orange Next button at the bottom of the page to go to the "Review and create" page.
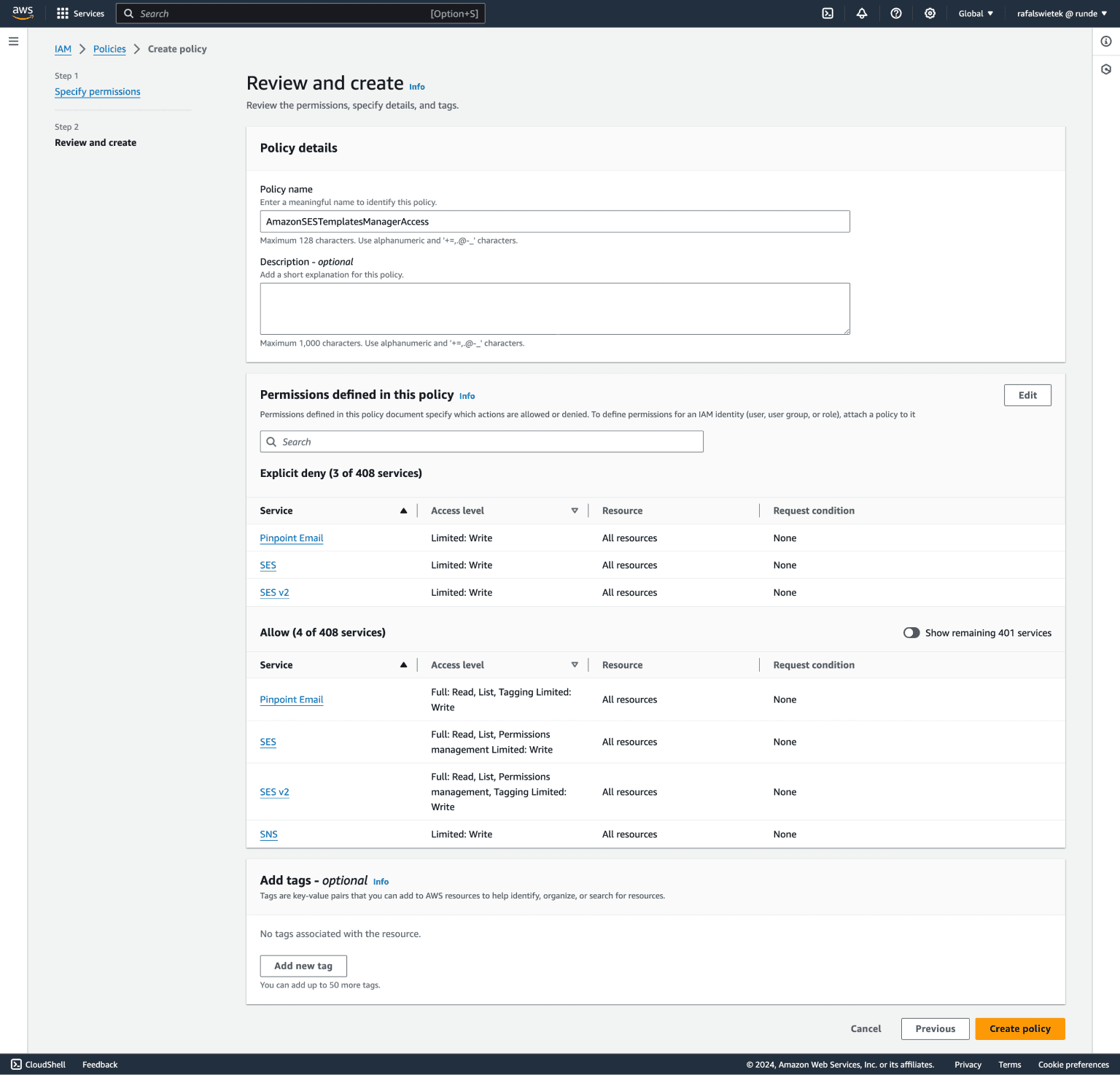
After making sure you're ok with the permissions you give create your new policy by clicking the orange Create policy button below the table.
Next, we can close the tab that was open to create the policy, and get back to the IAM user creation. We want to select a permissions policy that we just created, but to be able to find it on the list we will need to click the Refresh icon button which is next to the Create policy button.

When the list refreshes we can use the searcher to look for our new policy and mark it as checked. Then we can click the orange Next button to review all the user details we just set and confirm user creation.
Congratulations, the IAM User for the template manager is ready!
Generating credentials
The last thing we need is user credentials: Access key ID and Secret access key.
First, we need to click the name of a user we just created on the IAM user list. When the page with user details opens we need to select the Security credentials tab.
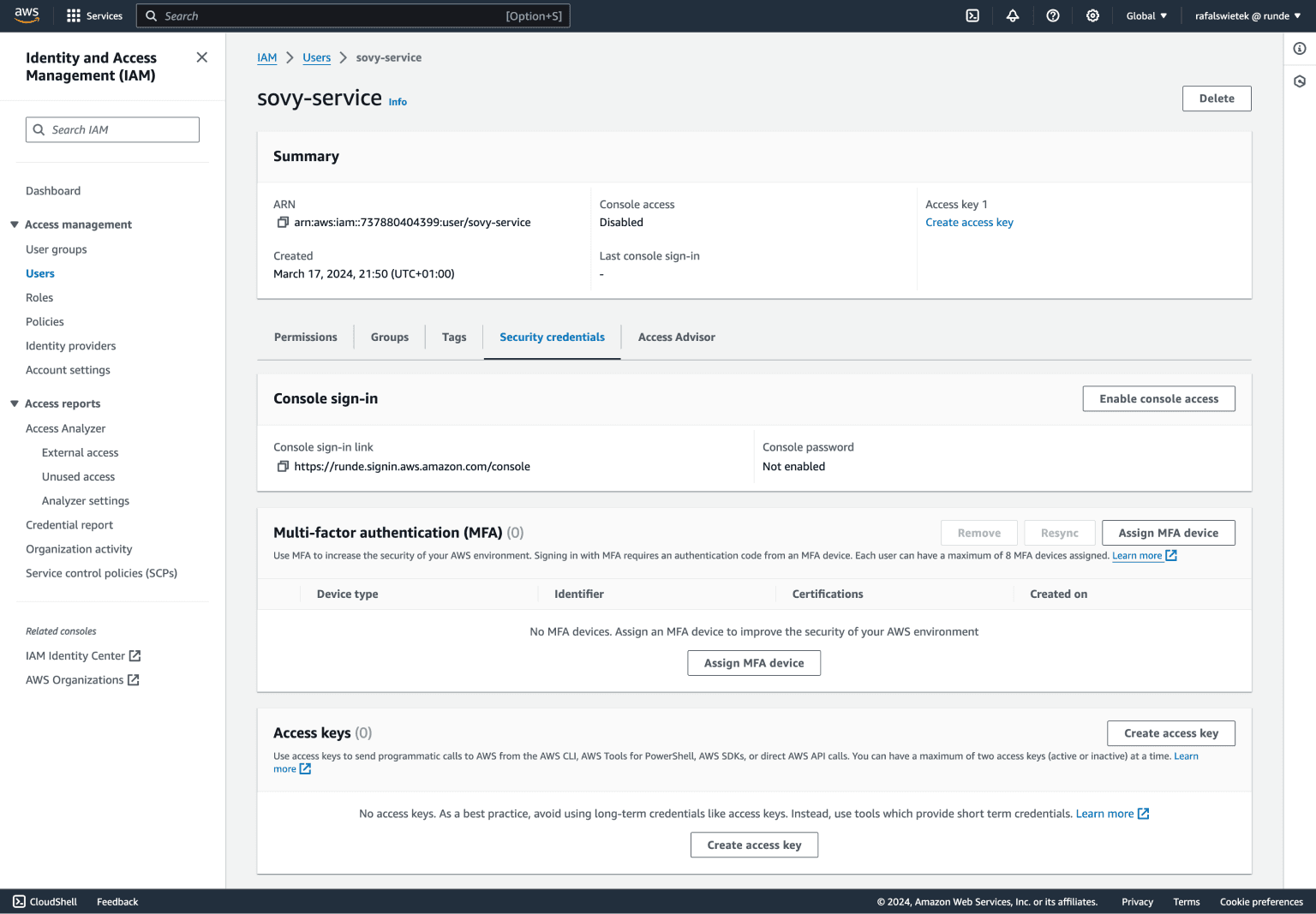
In this tab, we may need to scroll the page down a bit to find the Access keys section.
If this is a brand new user you just created you should not see any access keys on the list yet. Click the Create access key button to generate the first pair of credentials for this user.
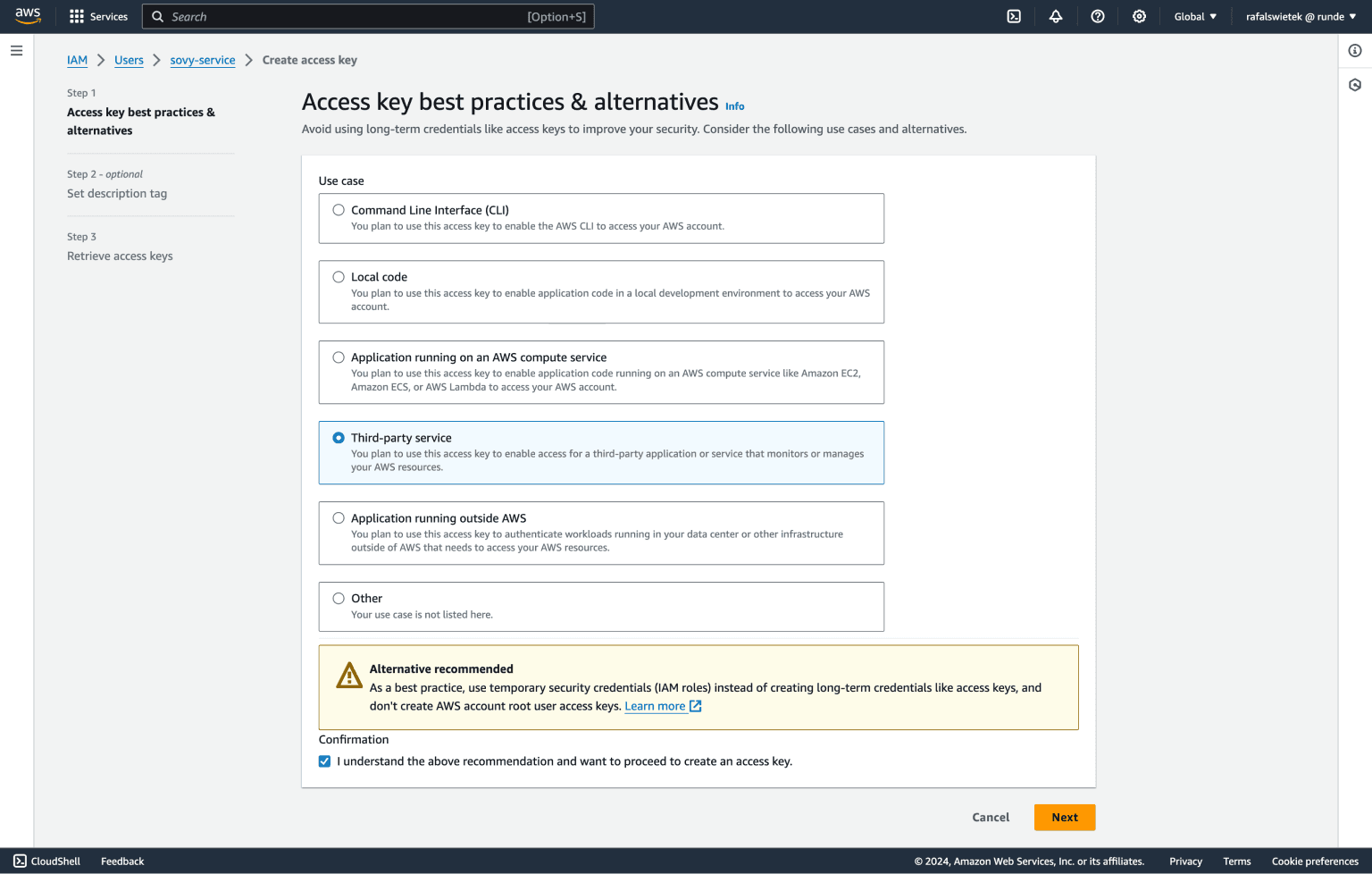
In the first step, you will be asked for a specific type of your use case - where exactly are you going to use these keys. It doesn't really matter which option you select, but you can select the Third-party service option as we consider Sovy - the template manager - to be a third-party service.
AWS will then propose an alternative that we're not gonna use so we need to check the confirmation that we understood their recommendation and click the orange Next button to move one.
The second step allows you to add some tags to your user. Tags are always optional in AWS and you can use them to organize your resources if you want. You can also just leave those fields empty and move on to the review.
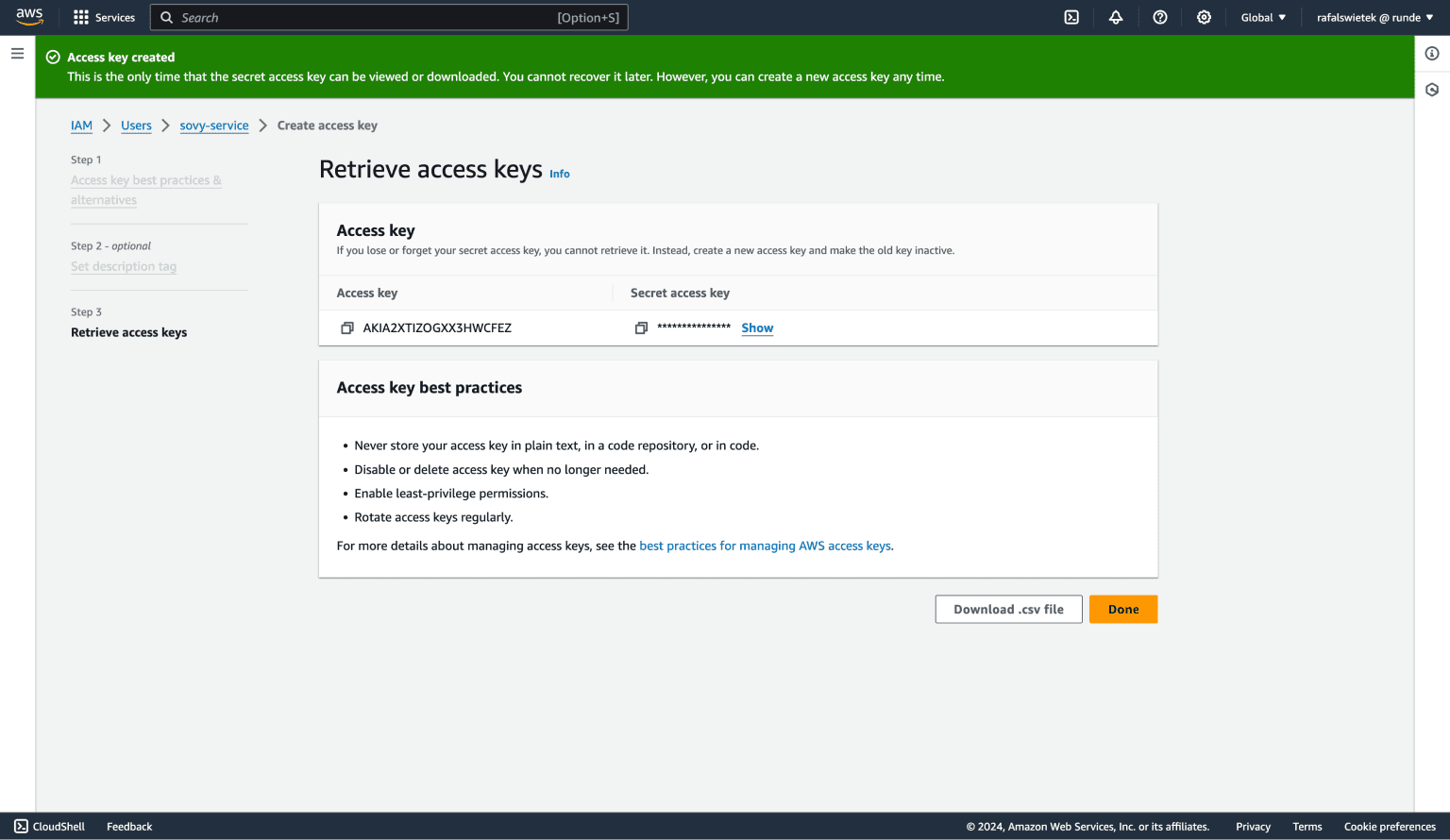
The review screen lets you see your generated credentials. Now, copy both Access key ID and Secret access key and save them locally, somewhere in your notes, just for a while. We're gonna need them to configure your Sovy account.
Remember - you should not share these credentials with anyone else. After you configure an AWS account in your Sovy account, you can remove them from your notes. You shouldn't need them ever again.
Summary
Well done! Now you know how to prepare the AWS IAM user and get credentials to connect your Amazon SES account with the email template manager Sovy.
You can check how to set up fresh Sovy account in this guide: How to use AWS SES email templates - Guide
If you think something is missing from this guide or something is not clear, please let me know at rafal@runde.pl.